This post was originally published by Matt Wrock on his blog, “Hurry Up and Wait: Tales from an automation engineer.”
This week Microsoft launched the release of Windows Server 2016 along with its ultra light headless deployment option – Nano Server. The Nano server images are many times smaller than what we have come to expect from a Windows server image. A Nano Vagrant box is just a few hundred megabytes. These machines also boot up VERY quickly and require fewer updates and reboots.
Earlier this year, I blogged about how to run a Chef client on Windows Nano Server. Things have come a long way since then and this post serves as an update. Now that the RTM Nano bits are out, we will look at:
- How to get and run a Nano server
- How to install the chef client on Windows Nano
- How to use Test-Kitchen and Inspec to test your Windows Nano Server cookbooks.
The sample cookbook I’ll be demonstrating here will highlight some of the new Windows container features in Nano server. It will install docker and allow you to use your Nano server as a container host where you can run, manipulate and inspect Windows containers from any Windows client.
How to get Windows Nano Server
You have a few options here. One thing to understand about Windows Nano is that there is no separate Windows Nano ISO. Deploying a Nano server involves extracting a WIM and some PowerShell scripts from a Windows 2016 Server ISO. You can then use those scripts to generate a .VHD file from the WIM or you can use the WIM to deploy Nano to a bare metal server. There are some shortcuts available if you don’t want to mess with the scripts and prefer a more instantly gratifying experience. Lets explore these scenarios.
Using New-NanoServerImage to create your Nano image
If you mount the server 2016 ISO (free evaluation versions available here), you will find a “NanoServer\NanoServerImageGenerator” folder containing a NanoServerImageGenerator PowerShell module. This module’s core function is New-NanoServerImage. Here is an example of using to to produce a Nano Server VHD:
Import-Module NanoServerImageGenerator.psd1
$adminPassword = ConvertTo-SecureString "vagrant" -AsPlainText -Force
New-NanoServerImage `
-MediaPath D:\ `
-BasePath .\Base `
-TargetPath .\Nano\Nano.vhdx `
-ComputerName Nano `
-Package @('Microsoft-NanoServer-DSC-Package','Microsoft-NanoServer-IIS-Package') `
-Containers `
-DeploymentType Guest `
-Edition Standard `
-AdministratorPassword $adminPasswordThis will generate a Nano Hyper-V capable image file of a Container/DSC/IIS ready Nano server. You can read more about the details and other options of this function in this TechNet article.
Direct EXE/VHD download
As I briefly noted above, you can download evaluation copies of Windows Server 2016. Instead of downloading a full multi gigabyte Windows ISO, you could choose the exe/vhd download option. This will download an exe file that will extract a pre-made vhd. You can then create a new Hyper-V VM from the vhd. With that vm, just login to the Nano console to set the administrative password and you are good to go.
Vagrant
This is my installation method of choice. I use a packer template to automate the download of the 2016 server ISO, the generation of the image file and finally package the image both for Hyper-V and VirtualBox Vagrant providers. I keep the image publicly available on Atlas via mwrock/WindowsNano. The advantage of these images is that they are fully patched (key for docker to work with Windows containers), work with VirtualBox and enable file sharing ports so you can map a drive to Nano.
Vagrant Nano bug
One challenge working with Nano Server and cross platform automation tools such as vagrant is that Nano exposes a PowerShell.exe with no -EncryptedCommand argument which many cross platform WinRM libraries leverage to invoke remote PowerShell on a Windows box.
Shawn Neal and I rewrote the WinRM ruby gem to use PSRP (PowerShell remoting protocol) to talk PowerShell and allow it to interact with Nano server. This has been integrated with all the Chef based tools and I will be porting it to Vagrant soon. In the meantime, a “vagrant up” will hang after creating the VM. Know that the VM is in fact fully functional and connectable. I’ll mention a hack you can apply to get Test-Kitchen‘s vagrant driver working later in this post.
Connecting to Windows Nano Server
Once you have a Nano server VM up and running. You will probably want to actually use it. Note: There is no RDP available here. You can connect to Nano and run commands either using native PowerShell Remoting from a Windows box (PowerShell on Linux does not yet support remoting) or use knife-windows‘ “knife winrm” from Windows, Mac or Linux.
PowerShell Remoting:
$ip = "<ip address of Nano Server>" # You only need to add the trusted host once Set-Item WSMan:\localhost\Client\TrustedHosts $ip # use usename and pasword "vagrant" on the mwrock vagrant box Enter-PSSession -ComputerName $ip -Credential Administrator
Knife-Windows:
# mwrock vagrant boxes have a username and password "vagrant" # add "--winrm-port 55985 for local VirtualBox knife winrm -m <ip address of Nano Server> "your command" --winrm-userator --winrm-password
Note that knife winrm expects “cmd.exe” style commands by default. Use “–winrm-shell powershell” to send powershell commands.
Installing Chef on Windows Nano Server
Quick tip: Do not try to install a chef client MSI. That will not work.
Windows Nano server jettisons many of the APIs and subsystems we have grown accustomed to in order to achieve a much more compact and cloud friendly footprint. This includes the removal of the MSI subsystem. Nano server does support the newer appx packaging system currently best known as the format for packaging Windows Store Apps. With Nano Server, new extensions have been added to the appx model to support what is now known as “Windows Server Applications” (aka WSAs).
At Chef, we have added the creation of appx packages into our build pipelines but these are not yet exposed by our Artifactory and Bintray fed Omnitruck delivery mechanism. That will happen but in the mean time, I have uploaded one to a public AWS S3 bucket. You can grab the current client (as of this post) here. To install this .appx file (note: if using Test-Kitchen, this is all done automatically for you):
- Either copy the .appx file via a mapped drive or just download it from the Nano server using this powershell function.
- Run “Add-AppxPackage -Path <path to .appx file>”
- Copy the appx install to c:\opscode\chef:
$rootParent = "c:\opscode"
$chef_omnibus_root - Join-Path $rootParent "chef"
if(!(Test-Path $rootParent)) {
New-Item -ItemType Directory -Path $rootParent
}
# Remove old version of chef if it is here
if(Test-Path $chef_omnibus_root) {
Remove-Item -Path $chef_omnibus_root -Recurse -Force
}
# copy the appx install to the omnibus_root. There are serious
# ACL related issues with running chef from the appx InstallLocation
# This is temporary pending a fix from Microsoft.
# We can eventually just symlink
$package = (Get-AppxPackage -Name chef).InstallLocation
Copy-Item $package $chef_omnibus_root -RecurseThe last item is a bit unfortunate but temporary. Microsoft has confirmed this to be an issue with running simple zipped appx applications. The ACLs on the appx install root are seriously restricted and you cannot invoke the chef client from that location. Until this is fixed, you need to copy the files from the appx location to somewhere else. We’ll just copy to the well known Chef default location on Windows c:\opscode\chef.
Running Chef
With the chef client installed, its easiest to work with chef when its on your path. To add it run:
$env:path += ";c:\opscode\chef\bin;c:\opscode\chef\embedded\bin" # For persistent use, will apply even after a reboot. setx PATH $env:path /M
Now you can run the chef client just as you would anywhere else. Here I’ll check the version using knife:
C:\dev\docker_nano_host [master]> knife winrm -m 192.168.137.25 "chef-client -v" --winrm-user vagrant --winrm-password vagrant 192.168.137.25 Chef: 12.14.60
Not all resources may work
I have to include this disclaimer. Nano is a very different animal than our familiar 2012 R2. I am confident that the newly launched Windows Server 2016 should work just as 2012 R2 does today, but nano has APIs that have been stripped away that we have previously leveraged heavily in Chef and InSpec. One example is Get-WmiObject. This cmdlet is not available on Nano Server so any usage that depends on it will fail.
Most of the crucial areas surrounding installing and invoking chef are patched and tested. However, there may be resources that either have not yet been patched or will simply never work. The windows_package resource is a good example. Its used to install MSIs and EXE installers not supported on Nano.
Test-Kitchen and InSpec on Nano
The WinRM rewrite to leverage PSRP allows our remote execution ecosystem tools to access Windows Nano Server. We have also overhauled our mixlib-install gem to use .Net core APIs (the .Net runtime supported on Nano) for the chef provisioners. With those changes in place, Test-Kitchen can install and run Chef, and InSpec can test resources on your Nano instances.
There are a few things to consider when using Test-Kitchen on Windows Nano:
Specifying the Chef appx installer
As I mentioned above, the “OmniTruck” system is not yet serving appx packages to Nano. However, you can tell Test-Kitchen in your .kitchen.yml to use a specific .msi or .appx installer. Here is some example yaml for running Test-Kitchen with Nano:
---
driver:
name: vagrant
provisioner:
name: chef_zero
install_msi_url: https://s3-us-west-2.amazonaws.com/nano-chef-client/chef-12.14.60.appx
verifier:
name: inspec
platforms:
- name: windows-nano
driver_config:
box: mwrock/WindowsNanoInspec requires no configuration changes.
Working around Vagrant hangs
Until I refactor Vagrant’s winrm communicator, it cannot talk PowerShell with Windows Nano. Because Test-Kitchen and InSpec talks to Nano directly via the newly PSRP supporting WinRM ruby gem, they make Vagrant’s limitation nearly unnoticeable. However the RTM Nano bits exacerbated the Vagrant bug causing it to hang when it does its initial winrm auth check. This can unfortunately hang your kitchen create. You can work around this by applying a simple “hack” to your vagrant install:
Update C:\HashiCorp\Vagrant\embedded\gems\gems\vagrant-1.8.5\plugins\communicators\winrm\communicator.rb (adjusting the vagrant gem version number as necessary) and change:
result = Timeout.timeout(@machine.config.winrm.timeout) do
shell(true).powershell("hostname")
endto:
result = Timeout.timeout(@machine.config.winrm.timeout) do
shell(true).cmd("hostname")
endThis should get your test-kitchen runs unblocked.
Running on Azure hosted Nano images
If you prefer to run Test-Kitchen and InSpec against an Azure hosted VM instead of vagrant, use Stuart Preston’s excellent kitchen-azurerm driver:
---
driver:
name: azurerm
driver_config:
subscription_id: 'your subscription id'
location: 'West Europe'
machine_size: 'Standard_F1'
platforms:
- name: windowsnano
driver_config:
image_urn: MicrosoftWindowsServer:WindowsServer:2016-Nano-Server-Technical-Preview:latest
See the kitchen-azurerm readme for details regarding azure authentication configuration. As of the date of this post, RTM images are not yet available but thats probably going to change very soon. In the meantime, use TP5.
Using Chef to Configure a Docker host
One of the exciting new features of Windows Server 2016 and Nano Server is their ability to host Windows containers. They can do this using the same Docker API we are familiar with with linux containers. You could walk through the official instructions for setting this up or you could just have Chef do this for you.
Updating the Nano server
Note that in order for this to work on RTM Nano images, you must install the latest Windows updates. My vagrant boxes come fully patched and ready but if you are wondering how do you install updates on a Nano server, here is how:
$sess = New-CimInstance -Namespace root/Microsoft/Windows/WindowsUpdate -ClassName MSFT_WUOperationsSession Invoke-CimMethod -InputObject $sess -MethodName ApplyApplicableUpdates
Then just reboot and you are good.
A sample cookbook to install and configure the Docker service
I converted the above mentioned instructions for installing Docker and configuring the service into a Chef cookbook recipe. Its fairly straightforward:
powershell_script 'install Nuget package provider' do
code 'Install-PackageProvider -Name NuGet -Force'
not_if '(Get-PackageProvider -Name Nuget -ListAvailable -ErrorAction SilentlyContinue) -ne $null'
end
powershell_script 'install nano container package' do
code 'Install-Module -Name xNetworking -Force'
not_if '(Get-Module xNetworking -list) -ne $null'
end
zip_path = "#{Chef::Config[:file_cache_path]}/docker.zip"
docker_config = File.join(ENV["ProgramData"], "docker", "config")
remote_file zip_path do
source "https://download.docker.com/components/engine/windows-server/cs-1.12/docker.zip"
action :create_if_missing
end
dsc_resource "Extract Docker" do
resource :archive
property :path, zip_path
property :ensure, "Present"
property :destination, ENV["ProgramFiles"]
end
directory docker_config do
recursive true
end
file File.join(docker_config, "daemon.json") do
content "{ \"hosts\": [\"tcp://0.0.0.0:2375\", \"npipe://\"] }"
end
powershell_script "install docker service" do
code "& '#{File.join(ENV["ProgramFiles"], "docker", "dockerd")}' --register-service"
not_if "Get-Service docker -ErrorAction SilentlyContinue"
end
service 'docker' do
action [:start]
end
dsc_resource "Enable docker firewall rule" do
resource :xfirewall
property :name, "Docker daemon"
property :direction, "inbound"
property :action, "allow"
property :protocol, "tcp"
property :localport, [ "2375" ]
property :ensure, "Present"
property :enabled, "True"
endThis downloads the appropriate Docker binaries, installs the Docker service and configures it to listen on port 2375.
To validate that all actually worked we have these InSpec tests:
describe port(2375) do
it { should be_listening }
end
describe command("& '$env:ProgramFiles/docker/docker' ps") do
its('exit_status') { should eq 0 }
end
describe command("(Get-service -Name 'docker').status") do
its(:stdout) { should eq("Running\r\n") }
endIf this all passes, we know our server is listening on the expected port and that Docker commands work.
Converge and Verify
So lets run these with kitchen verify:
C:\dev\docker_nano_host [master]> kitchen verify
-----> Starting Kitchen (v1.13.0)
-----> Creating <default-windows-nano>...
Bringing machine 'default' up with 'hyperv' provider...
==> default: Verifying Hyper-V is enabled...
==> default: Starting the machine...
==> default: Waiting for the machine to report its IP address...
default: Timeout: 240 seconds
default: IP: 192.168.137.25
==> default: Waiting for machine to boot. This may take a few minutes...
default: WinRM address: 192.168.137.25:5985
default: WinRM username: vagrant
default: WinRM execution_time_limit: PT2H
default: WinRM transport: negotiate
==> default: Machine booted and ready!
==> default: Machine not provisioned because `--no-provision` is specified.
[WinRM] Established
Vagrant instance <default-windows-nano> created.
Finished creating <default-windows-nano> (1m15.86s).
-----> Converging <default-windows-nano>...
…
Port 2375
✔ should be listening
Command &
✔ '$env:ProgramFiles/docker/docker' ps exit_status should eq 0
Command (Get-service
✔ -Name 'docker').status stdout should eq "Running\r\n"
Summary: 3 successful, 0 failures, 0 skipped
Finished verifying <default-windows-nano> (0m11.94s).
Ok our Docker host is ready.
Creating and running a Windows container
First if you are running Nano on VirtualBox, you need to add a port forwarding rule for port 2375. Also note that you will need the Docker client installed on the machine where you intend to run Docker commands. I’m running them from my Windows 10 laptop. To install docker on Windows 10:
Invoke-WebRequest "https://download.docker.com/components/engine/windows-server/cs-1.12/docker.zip" -OutFile "$env:TEMP\docker.zip" -UseBasicParsing Expand-Archive -Path "$env:TEMP\docker.zip" -DestinationPath $env:ProgramFiles $env:path += ";c:\program files\docker"
No matter what platform you are running on, once you have the Docker client, you need to tell it to use your Nano server as the docker host. Simply set the DOCKER_HOST environment variable to “tcp://<ipaddress of server>:2375”.
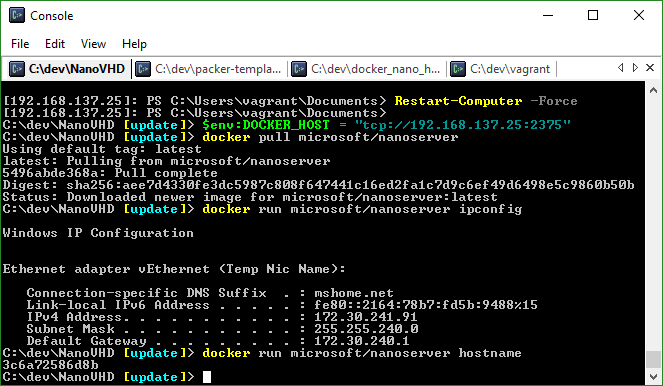
So now lets download a nanoserver container image from the docker hub repository:
C:\dev\NanoVHD [update]> docker pull microsoft/nanoserver Using default tag: latest latest: Pulling from microsoft/nanoserver 5496abde368a: Pull complete Digest: sha256:aee7d4330fe3dc5987c808f647441c16ed2fa1c7d9c6ef49d6498e5c9860b50b Status: Downloaded newer image for microsoft/nanoserver:latest
Now lets run a command…heck lets just launch an interactive PowerShell session inside the container with:
docker run -it microsoft/nanoserver powershell
Here is what we get:
Windows PowerShell Copyright (C) 2016 Microsoft Corporation. All rights reserved. PS C:\> ipconfig Windows IP Configuration Ethernet adapter vEthernet (Temp Nic Name): Connection-specific DNS Suffix . : mshome.net Link-local IPv6 Address . . . . . : fe80::2029:a119:3e4f:851a%15 IPv4 Address. . . . . . . . . . . : 172.30.245.4 Subnet Mask . . . . . . . . . . . : 255.255.240.0 Default Gateway . . . . . . . . . : 172.30.240.1 PS C:\> $env:COMPUTERNAME E1C534D94707 PS C:\>
Ahhwwww yeeeeaaaahhhhhhh.
What’s next?
So we have made a lot of progress over the last few months but the story is not entirely complete. We still need to finish knife bootstrap windows winrm and plug in our Azure extension.
Please let us know what works and what does not work. I personally want to see Nano server succeed and of course we intend for Chef to provide a positive Windows Nano Server configuration story.

